China is responsible for more hacking and IP theft of U.S. information and intellectual property than all other nations combined.
“The biggest threat we face as a country from a counter-intelligence perspective is from the People’s Republic of China,” United States FBI Director Christopher Wray told CBS recently, “and especially the Chinese Communist Party.”
“They are targeting our innovation, our trade secrets, our intellectual property on a scale that’s unprecedented in history. They have a bigger hacking program than that of every other major nation combined. They have stolen more of Americans’ personal and corporate data than every nation combined.
“It affects everything from agriculture to aviation to high tech to healthcare, pretty much every sector of our economy. Anything that makes an industry tick, they target.”
“China recognizes it needs to make leaps in cutting-edge technologies. But the sad fact is that instead of engaging in the hard slog of innovation, China often steals American intellectual property and then uses it to compete against the very American companies it victimized.”
Continues Wray: “We are now moving at a pace where we’re opening a new China counter-intelligence investigation about every 12 hours. There’s well north of 2,000 of these investigations. All 56 of our field offices are engaged on it. And I can assure you that it’s not because our agents don’t have enough else to do. It’s a measure of how significant the threat is.”
Diverse Techniques
“China uses a diverse range of sophisticated techniques—everything from cyber intrusions to corrupting trusted insiders,” Wray told the Hudson Institute in 2020. “They’ve even engaged in outright physical theft. And they’ve pioneered an expansive approach to stealing innovation through a wide range of actors—including not just Chinese intelligence services but state-owned enterprises, ostensibly private companies, certain kinds of graduate students and researchers, and a whole variety of other actors working on their behalf.
Economic Espionage
“To achieve its goals and surpass America, China recognizes it needs to make leaps in cutting-edge technologies. But the sad fact is that instead of engaging in the hard slog of innovation, China often steals American intellectual property and then uses it to compete against the very American companies it victimized—in effect, cheating twice over. They’re targeting research on everything from military equipment to wind turbines to rice and corn seeds.”
Unacceptable Behavior
Confronting this threat effectively does not mean we shouldn’t do business with the Chinese, says Wray. “It does not mean we shouldn’t host Chinese visitors. It does not mean we shouldn’t welcome Chinese students or coexist with China on the world stage. But it does mean that when China violates our criminal laws and international norms, we are not going to tolerate it, much less enable it.”
APT Winnti
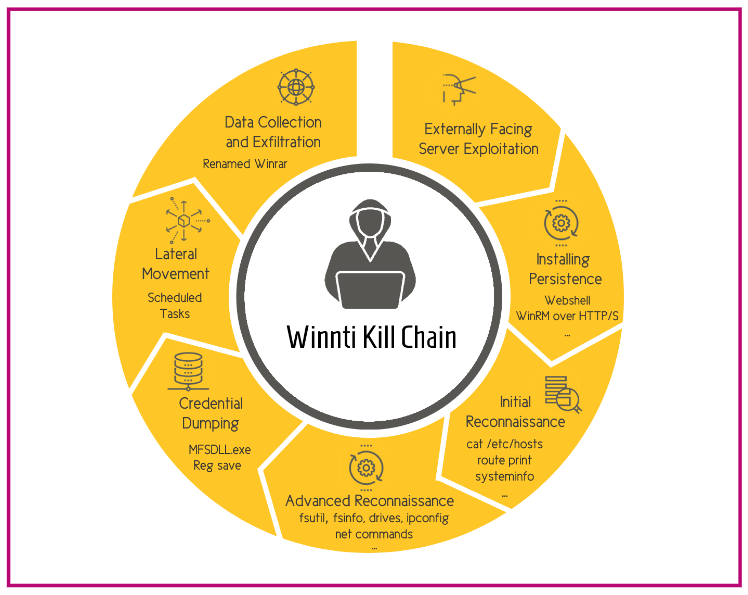
Researchers at Cybereason recently discovered an attack, which was assessed to be the work of Chinese APT Winnti. The security company briefed the US Federal Bureau of Investigation (FBI) and Department of Justice (DOJ) on the investigation into the malicious campaign, which Cybereason researchers dubbed Operation CuckooBees.
“Winnti, also known as APT 41, BARIUM, and Blackfly, is a Chinese state-sponsored APT (advanced persistent threat) group known for its stealth, sophistication, and focus on stealing technology secrets.”
For years, the campaign had operated undetected, siphoning intellectual property and sensitive data. The team published two reports–one that examines the tactics and techniques of the overall campaign and another that provides a more detailed analysis of the malware and exploits used.
“Those with more ambition than ethics prefer to invest effort and resources in stealing the IP of others rather than striving to develop their own innovations.”
“Intellectual property is also a prime target for both corporate and nation-state espionage,” reports Cybereason. “Despite the agreements and protections in place, those with more ambition than ethics prefer to invest effort and resources in stealing the intellectual property of others rather than striving to develop their own innovations.”
For a report related to Operation CuckooBees, including campaign tactics, techniques, and processes used, see Operation CuckooBees: Deep-Dive into Stealthy Winnti Techniques. For a detailed look at the malware toolkit employed in Operation CuckooBees, access Operation CuckooBees: A Winnti Malware Arsenal Deep-Dive.
Go here for the CBS “60 Minutes” interview with FBI Director Wray.
Image source: Hudson Institute; cybereason.com

