Legal Tug-Of-War: Protecting Privilege in Privacy Breach Disputes
IPilogue
MARCH 8, 2023
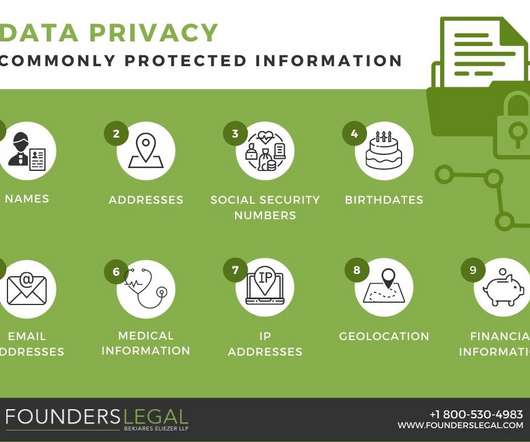
Privacy breaches are becoming commonplace in today’s business landscape and cybersecurity is top of mind for many organizations— and for good reason. This situation is exacerbated by the risk of litigation, as lawsuits are a legitimate consequence of a privacy breach. Kaplan v Casino Rama Services Inc.






































Let's personalize your content