How to Incorporate Privacy by Design Into Your Business
Olartemoure Blog
OCTOBER 11, 2021
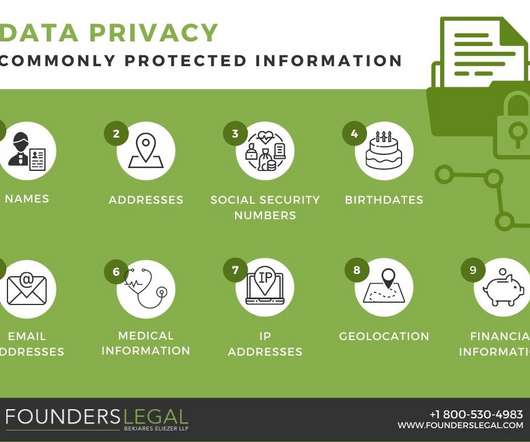
If you have a business, or a business idea in contemporary times, you will have to deal, one way or another, with user data. Do you want to have a webpage for your business? Privacy by Design is the integration of data processing procedures to every stage of business practices. European guidelines. Spam filters.













































Let's personalize your content